My Experience of Safeguarding the Indian Army Against Cyber Threats
Explore my journey in fortifying the Indian Army's cybersecurity framework. From countering cyber espionage to enhancing network resilience, this account delves into the strategies, challenges, and innovations that protected critical military infrastructure against evolving digital threats.

Strengthening the Indian Army’s Digital Security
Cybersecurity plays a crucial role in national defense, extending beyond traditional military operations to safeguarding sensitive digital assets. This case study highlights the discovery and responsible disclosure of a critical vulnerability in a Regimental Family Welfare Website linked to the Indian Army, emphasizing the importance of proactive security measures.
Discovering the Vulnerability: An Unexpected Opportunity
My familiarity with Indian Army websites, gained while preparing for SSB interviews, proved invaluable. Out of curiosity, I revisited a Regimental Family Welfare Website – a site technically part of the Indian Army infrastructure – to verify some information.
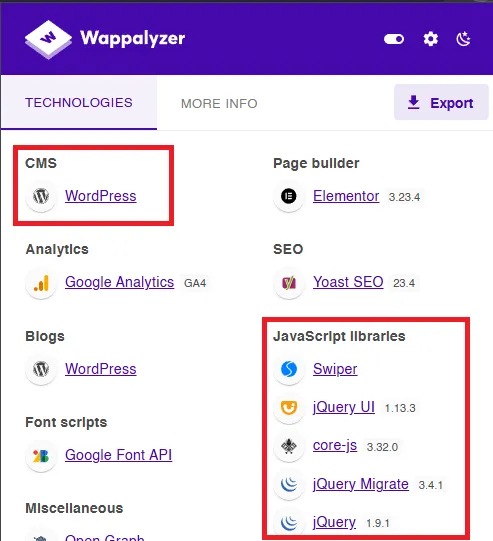
I was surprised to find the website running an outdated version of WordPress. Using Wappalyzer, I quickly identified the absence of a Content Delivery Network (CDN) or Web Application Firewall (WAF). As a cybersecurity enthusiast, this was a clear invitation to put my skills to the test.
Diving Deep: Exploitation and Discovery
I began by exploring the website's requests and endpoints using Burp Suite, but initially found nothing significant. The static nature of the site, with no login or signup options, seemed limiting. However, knowing it was built on WordPress, I decided to use WPScan to check for known vulnerabilities.
wpscan --url https://target.com --enumerate ap,at,u --api-token YOUR_API_TOKEN
-
--url: Specifies the target WordPress site URL. -
--enumerate: Enables detailed enumeration of plugins (ap), themes (at), and users (u). -
--api-token: Allows you to fetch vulnerability data from the WPScan database (requires a WPScan API token).
The scan revealed several Common Vulnerabilities and Exposures (CVEs) and outdated plugins. While many endpoints returned 404 (Not Found) or 403 (Forbidden) errors, I remembered the hacker's mantra: "What's denied is often worth exploring." Using a tool called 4-ZERO-3 (4-ZERO-3 Bypass), I dug deeper.


To my astonishment, I uncovered sensitive information, including names, photos, email addresses, residential addresses, ranks upon retirement, and dates of birth, belonging to veterans. This data was likely stored for communication purposes, but its exposure could lead to identity theft, phishing attacks, and other malicious activities.
Responsible Disclosure: From Hacker to Helper
Understanding the severity of the situation, I knew I had to act responsibly. I reported the vulnerability through the appropriate channels, including CERT-In (the Indian Computer Emergency Response Team). Given that the Regimental Centre was located in my hometown, I also decided to notify the concerned authorities directly.
I compiled a detailed report outlining the vulnerability, the exploitation process, and the nature of the exposed data. The next morning, I visited the Regimental Centre and requested a meeting with the senior officer (Adjutant).
An Unexpected Outcome: Pride and Recognition
During the meeting, I presented my findings and demonstrated the vulnerability's impact. The Adjutant, recognizing the seriousness of the issue, took me to the Deputy Commandant. After another detailed explanation, the Deputy Commandant made a surprising phone call – to my father.
Initially, I was anxious about the call. However, what followed exceeded my expectations. The officer told my father, "Sir, your son is a genius with a brilliant mind. We need more people like him in our nation. We are proud of him." Hearing those words brought tears to my eyes. It felt like a fulfillment of my dream to serve the armed forces, even if not in the traditional way.
We engaged in a fascinating discussion about my SSB experiences, cybersecurity, and the officers’ academy days. The officers expressed their appreciation for my efforts, presented me with a letter of appreciation, and encouraged me to continue contributing to the nation. Letter Of Acknowledgement
A Turning Point: Patriotism in the Digital Age
This experience was a pivotal moment in my life. While I may not have worn the uniform, I felt I had served my nation in my own way. It reaffirmed my belief that patriotism can be expressed in countless forms, extending beyond traditional roles.
To my fellow cybersecurity enthusiasts: keep learning, stay ethical, and contribute wherever you can. Every effort, no matter how small, can make the world a safer place.
Key Takeaways:
-
Outdated Software is a Risk: Regularly update software and plugins to patch known vulnerabilities.
-
Defense in Depth: Implement multiple layers of security, including CDNs and WAFs.
-
Ethical Hacking Matters: Responsible disclosure of vulnerabilities helps organizations improve their security posture.
-
Patriotism Takes Many Forms: Contributing to cybersecurity is a vital way to protect national interests.
Follow cyberdeepakyadav.com on
Facebook, Twitter, LinkedIn, Instagram , and YouTube
What's Your Reaction?
























